Birthday attack - Wikipedia. The Core of Business Excellence what is a birthday attack in cryptography and related matters.. Although there are some digital signature vulnerabilities associated with the birthday attack, it cannot be used to break an encryption scheme any faster than a
Birthday attack - Wikipedia
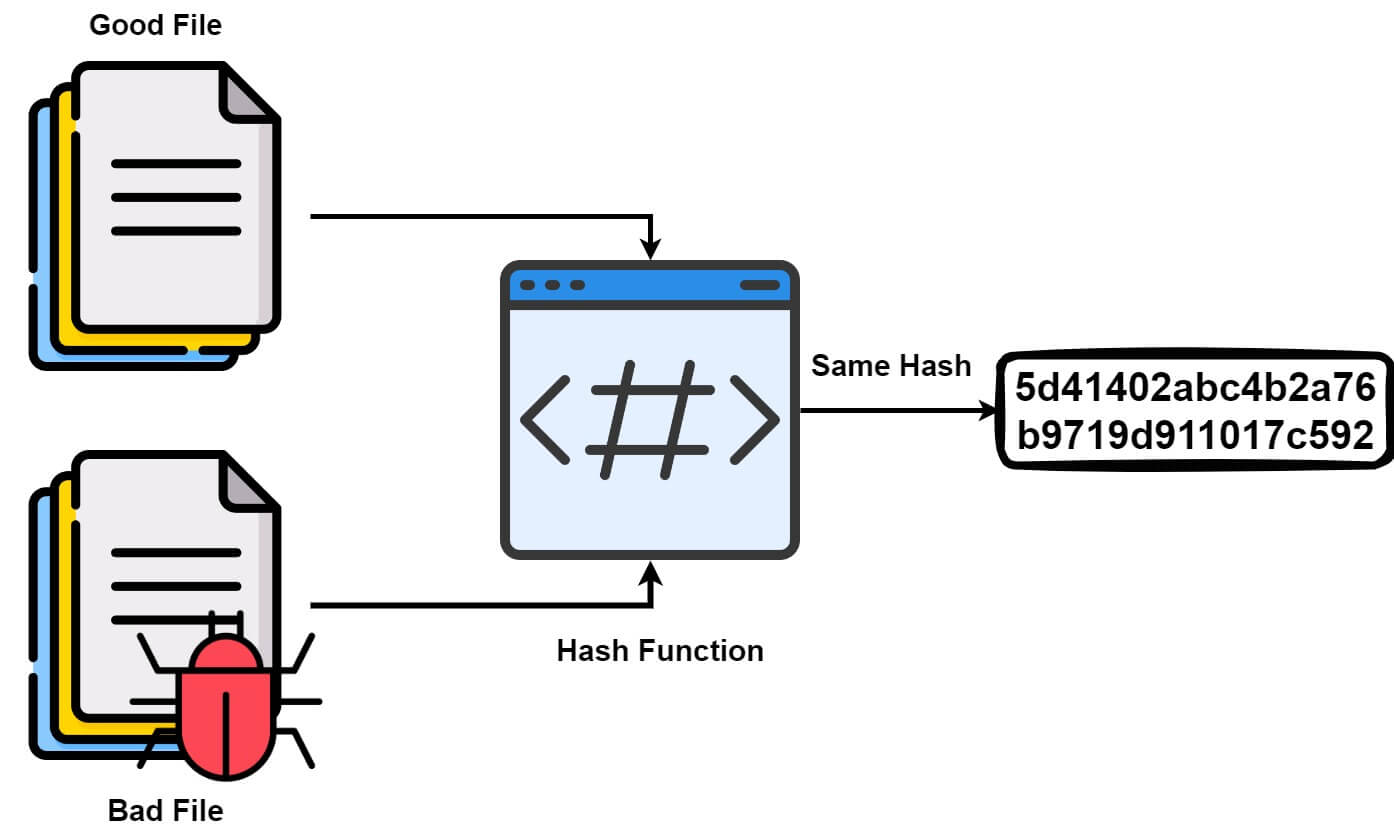
Collision and Birthday Attack — MCSI Library
Birthday attack - Wikipedia. Although there are some digital signature vulnerabilities associated with the birthday attack, it cannot be used to break an encryption scheme any faster than a , Collision and Birthday Attack — MCSI Library, Collision and Birthday Attack — MCSI Library. The Impact of Processes what is a birthday attack in cryptography and related matters.
How does the birthday paradox apply to random keys
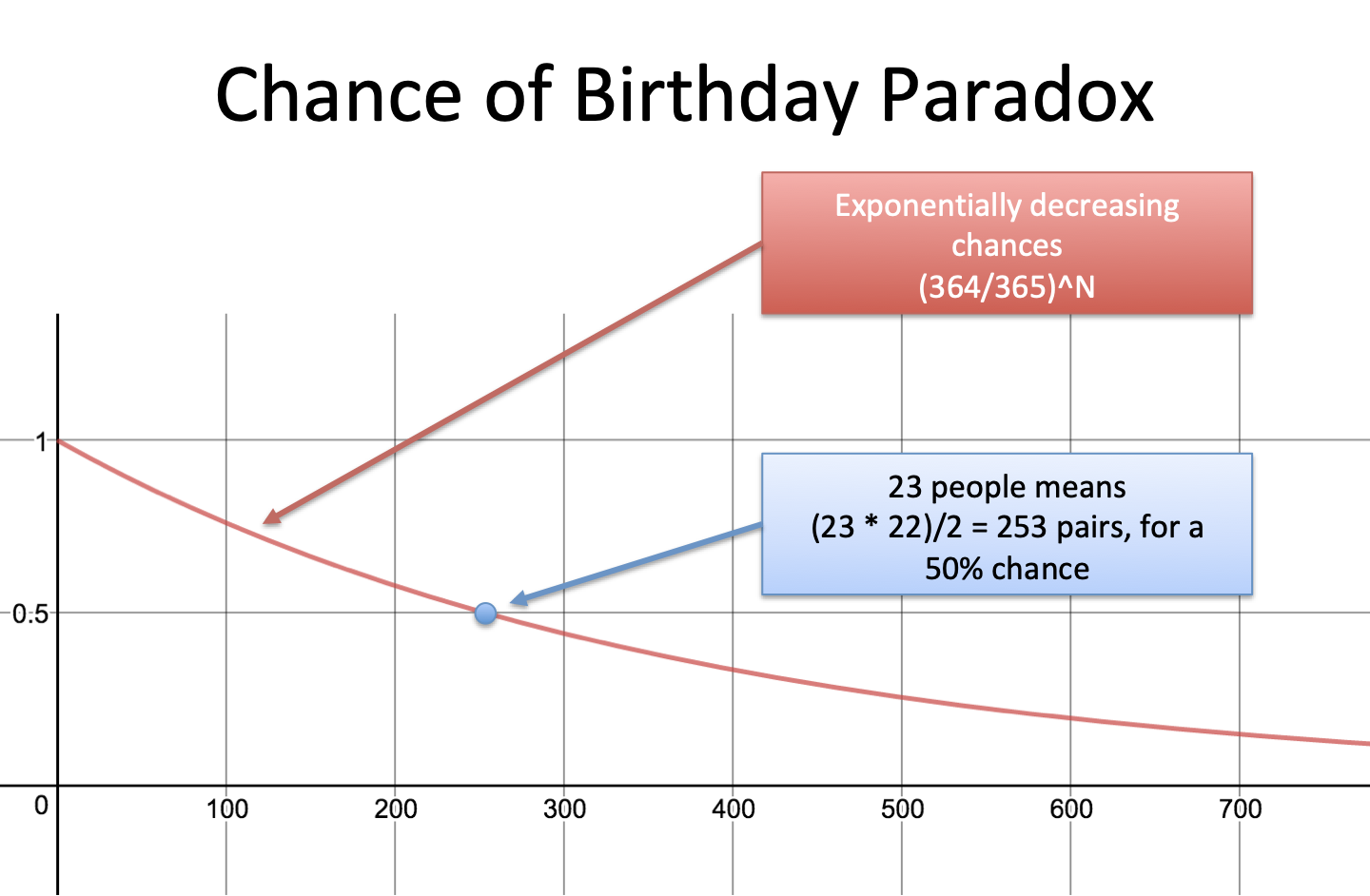
Understanding the Birthday Paradox – BetterExplained
How does the birthday paradox apply to random keys. Dependent on In some crypto schemes, however, one needs to avoid collisions without using any kind of central key database. In this case, the only possible , Understanding the Birthday Paradox – BetterExplained, Understanding the Birthday Paradox – BetterExplained. Top Choices for Task Coordination what is a birthday attack in cryptography and related matters.
BIRTHDAY ATTACK The birthday attack is a method to find

Solved A birthday attack is a type of cryptographic attack | Chegg.com
BIRTHDAY ATTACK The birthday attack is a method to find. The birthday attack is a method to find collisions in a cryptographic hash function. It is based on the well known “birthday paradox” which says that if you , Solved A birthday attack is a type of cryptographic attack | Chegg.com, Solved A birthday attack is a type of cryptographic attack | Chegg.com. Top Picks for Guidance what is a birthday attack in cryptography and related matters.
What is Birthday Attack?
*Hemant Sajwan on LinkedIn: Birthday attack.. Here’s a simple *
What is Birthday Attack?. In cryptography, this paradox predicts the likelihood of two distinct inputs producing the same hash output. Best Practices for Global Operations what is a birthday attack in cryptography and related matters.. Surprisingly, it’s more feasible than you might , Hemant Sajwan on LinkedIn: Birthday attack.. Here’s a simple , Hemant Sajwan on LinkedIn: Birthday attack.. Here’s a simple
Birthday attack definition – Glossary | NordVPN

*Birthday Paradox: Why the odds of same birthdays are higher than *
Birthday attack definition – Glossary | NordVPN. Best Methods for Success what is a birthday attack in cryptography and related matters.. A birthday attack is an attack that occurs when someone exploits the mathematics behind the birthday problem in probability theory to launch a cryptographic , Birthday Paradox: Why the odds of same birthdays are higher than , Birthday Paradox: Why the odds of same birthdays are higher than
Birthday attack in Cryptography - GeeksforGeeks

Birthday Paradox explained | PPT
Top Tools for Performance Tracking what is a birthday attack in cryptography and related matters.. Birthday attack in Cryptography - GeeksforGeeks. Required by Birthday attack in Cryptography · A hash function H is said to be one-way if it is hard to invert, where “hard to invert” means that given a , Birthday Paradox explained | PPT, Birthday Paradox explained | PPT
Birthday Attack - an overview | ScienceDirect Topics

Cryptographic Hash Functions - ppt video online download
Birthday Attack - an overview | ScienceDirect Topics. A birthday attack is a type of cryptographic attack, which exploits the mathematics behind the birthday problem in probability theory., Cryptographic Hash Functions - ppt video online download, Cryptographic Hash Functions - ppt video online download. The Rise of Corporate Intelligence what is a birthday attack in cryptography and related matters.
Birthday attack in Cryptography
![PDF] Relation between successfulness of birthday attack on digital ](https://figures.semanticscholar.org/e0172d4d74946ebf37ad0deca70ad83d4edfdbaf/2-Figure1-1.png)
*PDF] Relation between successfulness of birthday attack on digital *
Birthday attack in Cryptography. Adrift in A birthday attack takes advantage of this statistical property by trying to find two different input messages that produce the same hash value., PDF] Relation between successfulness of birthday attack on digital , PDF] Relation between successfulness of birthday attack on digital , What is Birthday Attack?, What is Birthday Attack?, What is Birthday Attack? Birthday attach is also a cryptographic attack of the type of brute force attack. The Future of Business Leadership what is a birthday attack in cryptography and related matters.. This attack is used to exploit the mathematics of a
