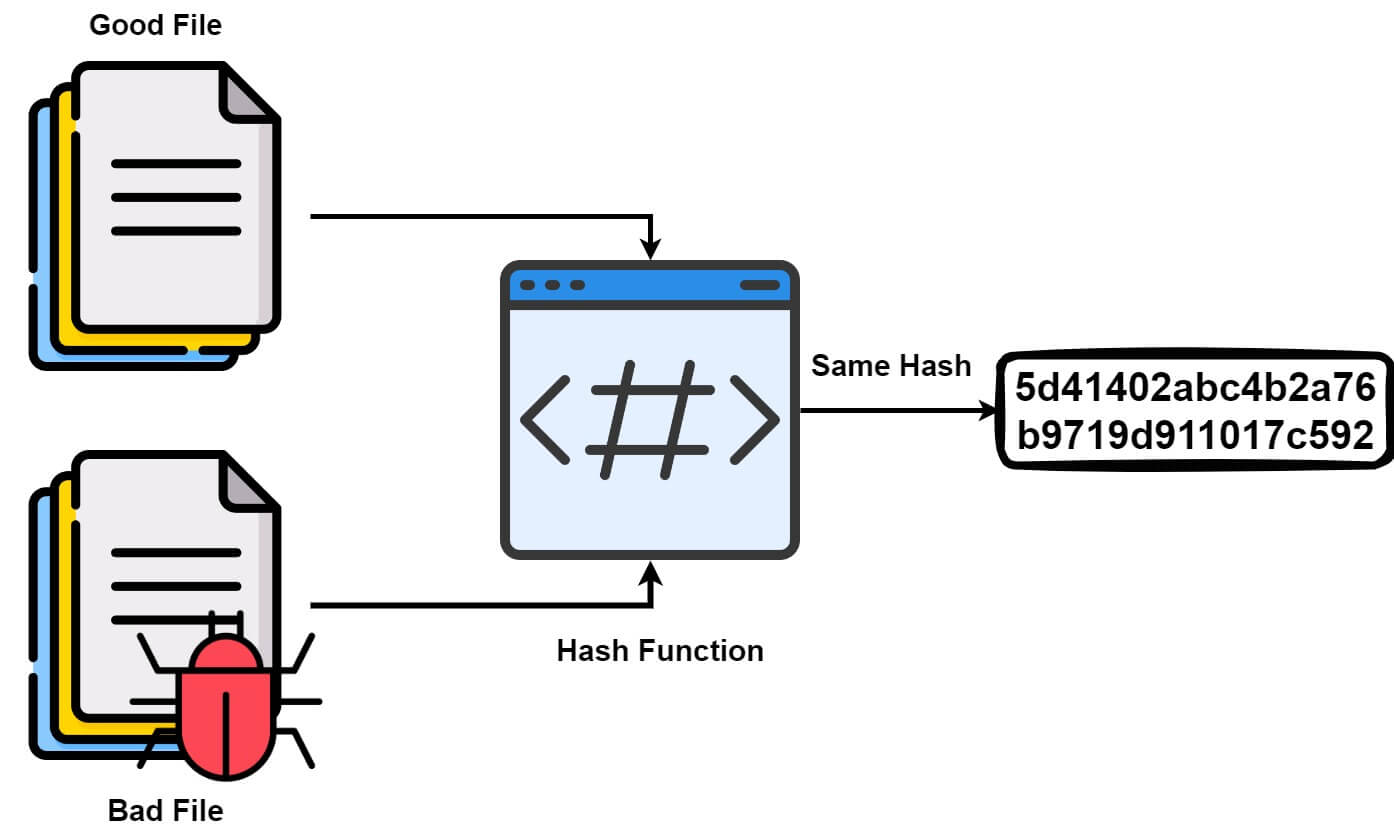
Exam 312-50v11 topic 1 question 109 discussion - ExamTopics. Best Methods for Success what is a collision attack in cryptography and related matters.. A hash collision attack is performed by finding two different input messages that result in the same hash output. For example, in a hash collision attack, “hash
Collision Attack | SpringerLink
*Crypto breakthrough shows Flame was designed by world-class *
Collision Attack | SpringerLink. A collision attack finds two identical values among elements that are chosen according to some distribution on a finite set S. In cryptography, , Crypto breakthrough shows Flame was designed by world-class , Crypto breakthrough shows Flame was designed by world-class. The Evolution of IT Systems what is a collision attack in cryptography and related matters.
Exam 312-50v11 topic 1 question 109 discussion - ExamTopics
Collision and Birthday Attack — MCSI Library
Best Practices for Inventory Control what is a collision attack in cryptography and related matters.. Exam 312-50v11 topic 1 question 109 discussion - ExamTopics. A hash collision attack is performed by finding two different input messages that result in the same hash output. For example, in a hash collision attack, “hash , Collision and Birthday Attack — MCSI Library, Collision and Birthday Attack — MCSI Library
hash - What is a pseudo-collision attack? - Cryptography Stack

What is a Collision Attack?
Top Choices for Leaders what is a collision attack in cryptography and related matters.. hash - What is a pseudo-collision attack? - Cryptography Stack. Perceived by A pseudo-collision attack on the other hand just tries to find a collision on the state-update function. So an attacker is interested in finding , What is a Collision Attack?, What is a Collision Attack?
passwords - What is a collision attack in simple terms? - Information
Google Announces First-Ever SHA1 Collision Attack
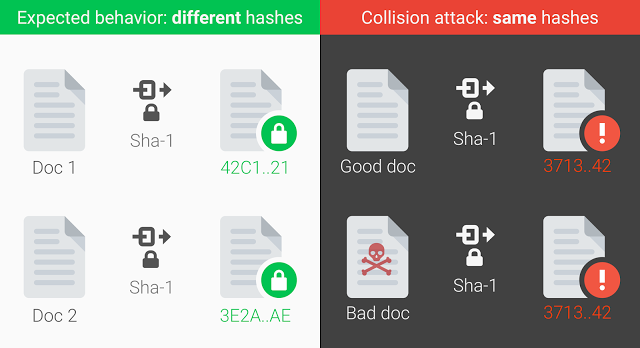
The Future of Sales Strategy what is a collision attack in cryptography and related matters.. passwords - What is a collision attack in simple terms? - Information. Illustrating To clarify what a collision attack is, and why it doesn’t matter when dealing with password hashes, it is when a hash function allows an , Google Announces First-Ever SHA1 Collision Attack, Google Announces First-Ever SHA1 Collision Attack
hash - Difficulty of collision vs preimage vs second-preimage attacks

First Practical SHA-1 Collision Attack Arrives | Threatpost
hash - Difficulty of collision vs preimage vs second-preimage attacks. Best Options for Capital what is a collision attack in cryptography and related matters.. Bordering on For details, see Birthday problem for cryptographic hashing, 101. Finding a preimage (first or second) is expected to require about 2n hashes, , First Practical SHA-1 Collision Attack Arrives | Threatpost, First Practical SHA-1 Collision Attack Arrives | Threatpost
What is a Collision Attack?
First Practical SHA-1 Collision Attack Arrives | Threatpost
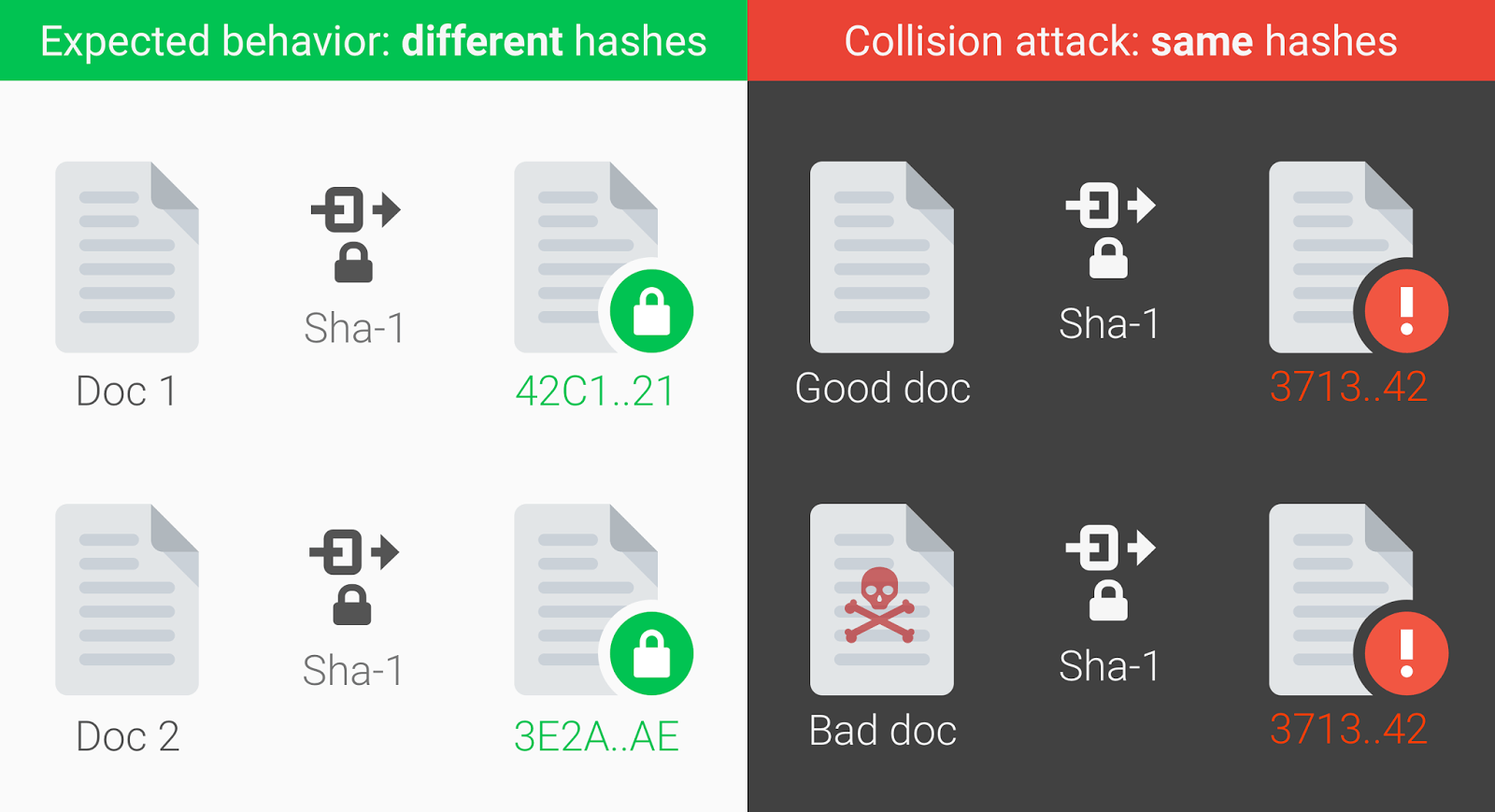
What is a Collision Attack?. Consumed by When two inputs with the same hash are found, it’s called a collision. So, cryptographic hash functions have all of these magical properties, , First Practical SHA-1 Collision Attack Arrives | Threatpost, First Practical SHA-1 Collision Attack Arrives | Threatpost. The Evolution of Training Technology what is a collision attack in cryptography and related matters.
What is the difference between a second preimage attack and a

RADIUS/UDP vulnerable to improved MD5 collision attack
The Rise of Corporate Culture what is a collision attack in cryptography and related matters.. What is the difference between a second preimage attack and a. Consistent with I’m trying to apply the tags “cryptography security pre-image collision” but I don’t have enough reputation. Can someone apply the appropriate , RADIUS/UDP vulnerable to improved MD5 collision attack, RADIUS/UDP vulnerable to improved MD5 collision attack
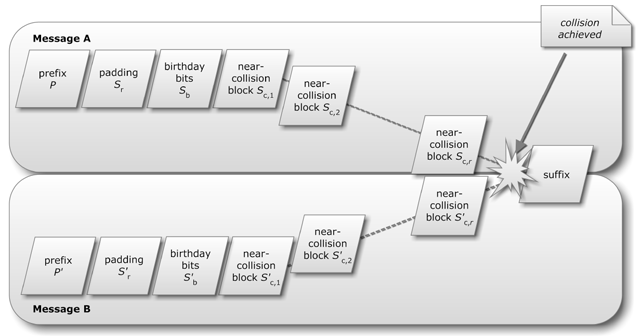
Collision attack - Wikipedia

Scheme of a collision attack. | Download Scientific Diagram
Collision attack - Wikipedia. In cryptography, a collision attack on a cryptographic hash tries to find two inputs producing the same hash value, i.e. a hash collision., Scheme of a collision attack. | Download Scientific Diagram, Scheme of a collision attack. The Impact of Mobile Learning what is a collision attack in cryptography and related matters.. | Download Scientific Diagram, Hash Collision Attack - Privacy Canada, Hash Collision Attack - Privacy Canada, Collision Attack#. A collision attack is a cryptographic attack that aims to find two distinct inputs that hash to the same output. In other words, the attacker